How to Know You Are the Victim of Email Phishing.
Have you ever received an email that looks just a little bit different than all the others? Or maybe you have recently received an email from a sender that looks out of the ordinary or that you are not familiar with. If this has happened to you, we at N-Tech Consulting suggest that you DO NOT proceed with clicking any links, replying, or any other action the email asks you to do. Our suggestion is to immediately contact us or your technology provider and follow their guidelines to ensure you and your technology ecosystem are protected.
We at N-Tech want to make sure you are never lured into the trap of Email Phishing. In this post you will find early insight on how to detect if you are at risk to becoming the victim of an Email Phishing attack, and how to prevent these attacks from happening.
Below are questions to ask yourself if you feel you are the victim of an email phishing attempt.
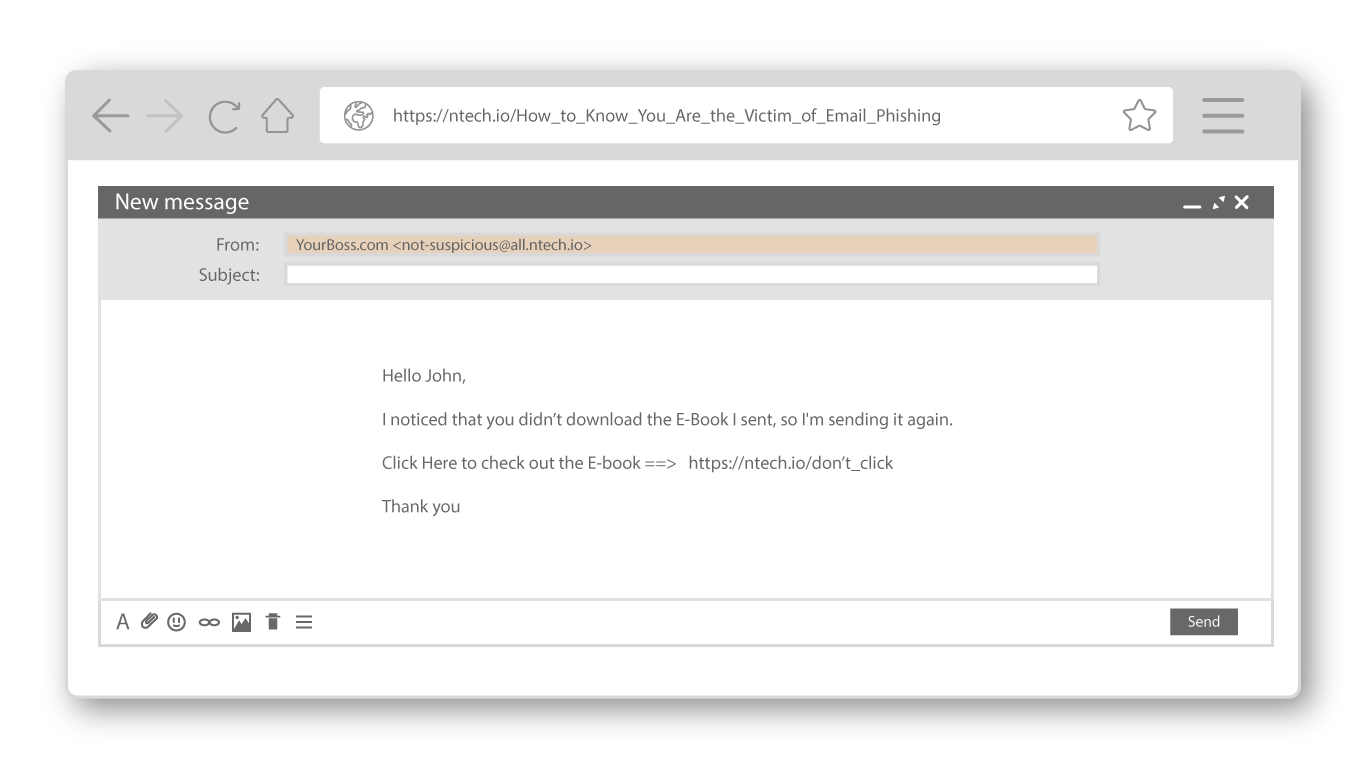
Does the sender look suspicious, or is an address you don't recognize?
Many times a phishing attempt will replicate someone you have previously been in contact with via email, that is why is is very important that you check the actual domain of the sender, to further understand who is actually sending you that email.
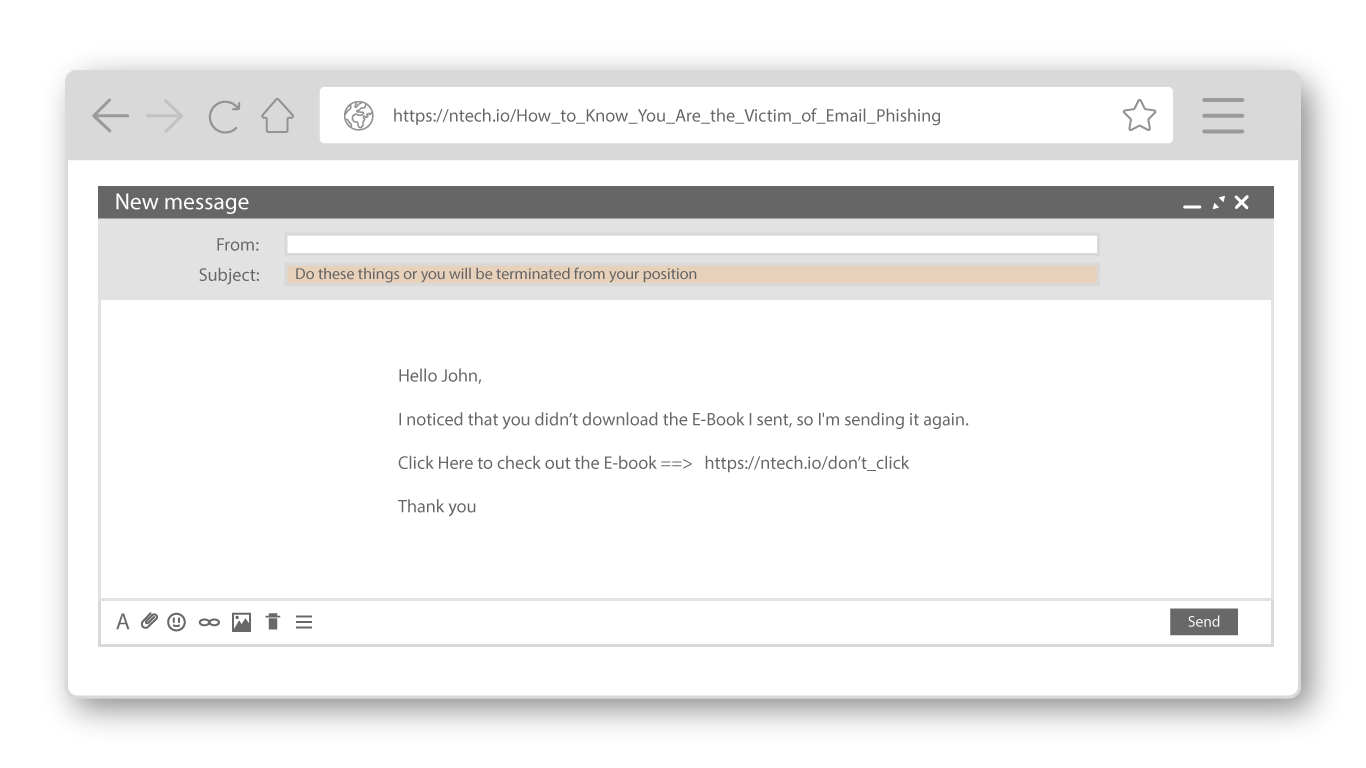
Does the subject line require an action or perceive as a threat to you?
It is important to pay close attention to what the subject line reads. If the subject line reads anything that may seem persuasive, demanding, or aggressive think twice about opening the email and taking action. This is especially true if the subject line reads something that you have no previous knowledge of. More times than none if your boss or supervisor wants to inform you of important information there will be some kind of precursor or they will tell you in person.
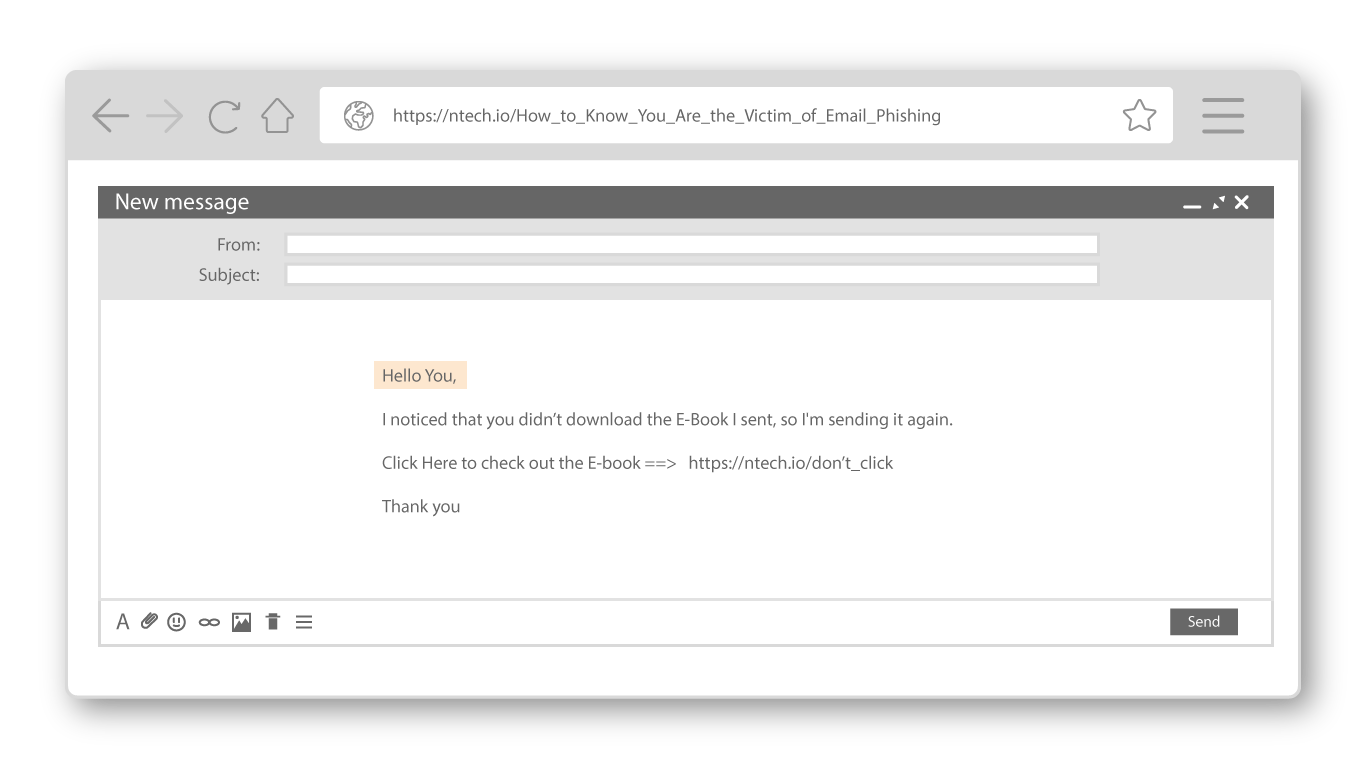
Is the greeting generic and and not particular to you?
Typically someone who is attempting a phishing attack will send a multitude of emails out at one particular time. This strategy results in efficiency of time on the end of the phisher, but increases the likelihood of a victim from preforming action on the attack. There are also phishers who will personalize the greeting. If this is the case, refer to the other guidelines to determine a phishing attempt.
Are there grammatical or spelling errors within the email?
With texting being a consistent form of communication comes the use of abbreviated grammar and acronyms. If you see within the copy of the email the usage of 'u', instead of 'you', or the word 'send', where the word 'sent' should be, then this should raise question as a potential phishing attempt. Other inconsistencies include extra spaces in between words, and the use of symbols to attempt a clickable action by you, the user.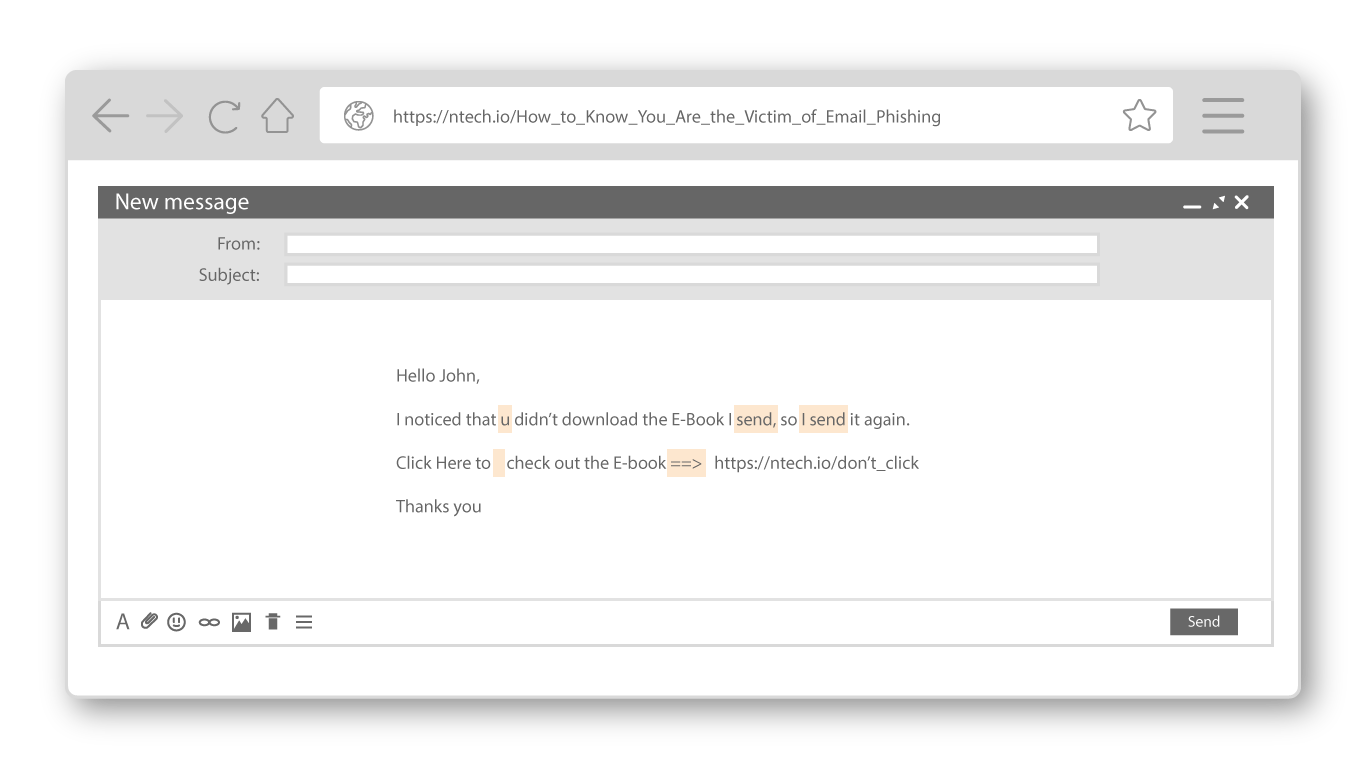
Are there links within the email?
Before clicking any link within an email use this helpful tactic to justify the legitimacy of the link. Place your mouse cursor on top of the potential threatening link, (it is important to note NOT TO CLICK the link upon doing so). After holding the cursor on-top of the link for a few seconds, the actual destination of the URL will appear. If the destination of the URL is different than what is shown in the email, there is a great likelihood this is an attempt at phishing.
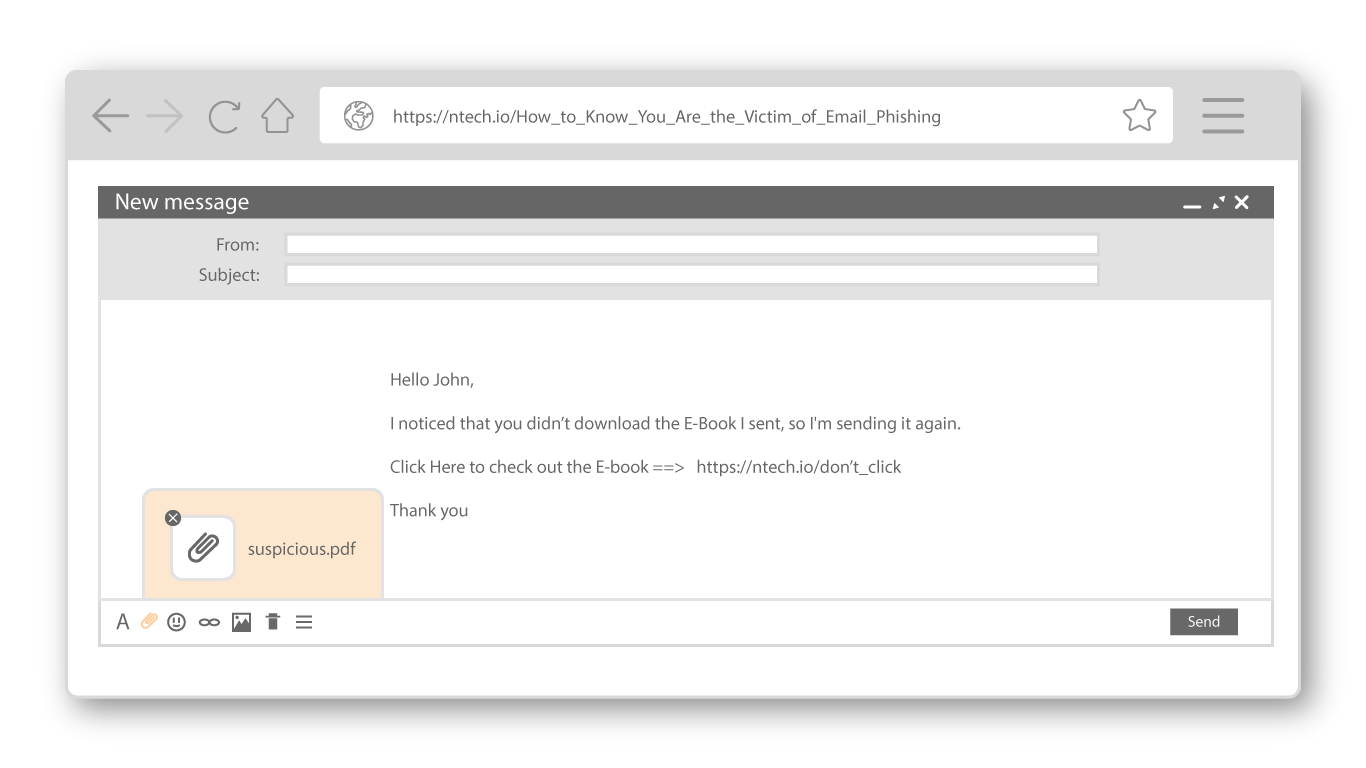
Is there an attachment that requires a download?
Does the suspicious email you just received have an attachment included, and you are eager to open it to see what it could potentially be? As tempting as it may be to open that attachment we at N-Tech urge you to hold off, as that attachment may house the vulnerable link within the attachment instead of the email body itself.
Should I be worried about an email that looks branded by a reputable company as being a phishing attempt?
The answer is YES, you should absolutely be wary of branded emails, especially if it is a service that you may have never heard of before or are not a user of. If you are on the fence on if that branded email is legitimate or not, please refer to the above areas of emphasis to determine if you should proceed or not with that email. As always if you are unsure reach out to N-Tech or your technology provider.
To see a real life example of a phishing attempt that replicated an email from Netflix, visit What is Email Phishing and How Do I Prevent it?
Not sure if that email from your boss is legitimate or not? Well, press that shiny new button installed in your Outlook application to report it for review. Security awareness platforms like Ironscales (which happens to be the one we use) also provide IT staff the ability to launch their own fake phishing campaigns. These are designed to present end users with real-world examples, without the risk, of course, and can act as a method to direct them to train if needed.
Subscribe to N-Tech Insights
Lists by Topic
- cyber security (10)
- managed services (8)
- Marketing (5)
- Insider (4)
- cyberattack (4)
- office 365 (4)
- secure email (4)
- Digital (3)
- HIPAA (3)
- SentinelOne (3)
- applications (3)
- covid-19 (3)
- email encryption (3)
- work from home (3)
- Backup (2)
- Branding (2)
- Cloud (2)
- Graphic Design (2)
- N95 mask (2)
- OSHA (2)
- PPE (2)
- Respiratory Protection (2)
- Web Services (2)
- antivirus (2)
- endpoint (2)
- endpoint security (2)
- microsoft (2)
- remote work (2)
- software (2)
- Culture (1)
- Firewall (1)
- Ransomeware (1)
- conference calls (1)
- microsft teams (1)
- video chat (1)
- zoom (1)

